2021 Security Series (Part 1)
Accounts we are hearing coming out of Afghanistan at this time reveal that Taliban fighters are checking Afghani’s mobile devices. Anyone found with a digital version of a Bible are reportedly being executed. Additionally, western citizens like Americans, British, and others are using computers and the internet to attempt to coordinate evacuations and rescues for themselves and our Afghan allies are in great peril. Getting caught can mean immediate death for all parties involved.
Missionaries, journalists, activists, or anyone working in restrictive areas around the world, must take security very seriously when it comes to internet activity and communications, and when identities must be protected. This includes securing data should it become lost, confiscated, or stolen. Compromised information could mean the difference between life or death — freedom or incarceration.
TAILS operating system provides the tools that many citizens are looking for in today’s dangerous socio-political climate:
- Internet anonymity
- Security
- Encryption features
- FREE and easy-to-download and set-up
- All activity is wiped and non-recoverable upon powering down or unplugging
- A secure computer operating system you can carry in your pocket and boot from almost any computer/laptop
- Secure, encrypted persistent drive option for safely storing some of your files and settings
As mentioned in the RFR podcasts, Episode 21-27, TAILS is ‘The Amnesic Incognito Live System’, for secure, encrypted, and anonymous internet activity.
TAILS can be installed and ran from most standard, quality portable flash drives (many Sandisk brands have reportedly been ‘glitchy’, so we recommend avoiding them).

And much easier to conceal, micro SD cards (with adapters) are a great option:

Below are two tutorial videos to introduce you to TAILS, as well as step-by-step installation. However, I recommend the RUFUS disk writing application for writing ISO images to removable media, as is included in the setup guide at the bottom of this post, by Hotel Charlie-08.
The Center for Investigative Journalism in London has produced a series of TAILS videos, by INFOSEC Bytes.
I highly recommend watching them all!
INTRODUCTION TO TAILS (by INFOSEC Bytes)
Getting TAILS (by INFOSEC Bytes)
=== The following step-by-step guide was provided by AmRRON Corps operator, Hotel Charlie-08. Thank you! ===
Hopefully I can assist new to linux-based operating systems folks to create a bootable drive on their current windows machine with this follow guide.
First off, I would like to mention that, technically, linux is actually not an operating system, but a kernel subsystem that someone, anyone can create or place an operating system on top of it. A kernel is sort of like the interface between the OS user interface and the actual machine that it is working on. Sort of like a GM chassis that gets engineered, and then chev, buick, cadillac etc all place there distinctive bodywork on top of the chassis. All you see is the bodywork UI, and you can control (drive) the chassis.
All operating systems has Kernels
Windows sits the WINNT kernel
Apples OS sits on the Darwin or BSD kernel
*BSDs OSs sits there own BSD kernels
Linuxmint, Ubuntu, Debian, TAILs, Android, etc,…. sits on the linux kernel
So if you want to impress your friends, tell them that you use a “linux-based” operating system. LOLOLOL
We will be using RUFUS as our image burner. When on a windows machine, I do recommend rufus as an image burner, because it tends to review the ISO and then download the extra files if needed to make the ISO bootable from EUFI or legacy BIOS’d machines more easier. Although most of todays ISOs have this already embedded
This can be done with any Operating system ISOs, but right now, we will focus on TAILS, as mentioned on JJS’s podcasts
I do recommend using 16gigs Flash drive or more for this, especially if you want persistence.
So the first step is to download the TAILS image (ISO)

In order to make sure that you have a valid download, follow the pgp verification steps on the site after downloading the image.

After verifying successfully, you can close this site.
Next up, download RUFUS application from the website.

Once downloaded, we can proceed to the location or folder where you downloaded RUFUS. Right click on the RUFUS application and select “Run as Administrator”

This will open the RUFUS application, Select the Flash drive in the “Device” drop down menu, then press the “select” button and select the TAILS ISO
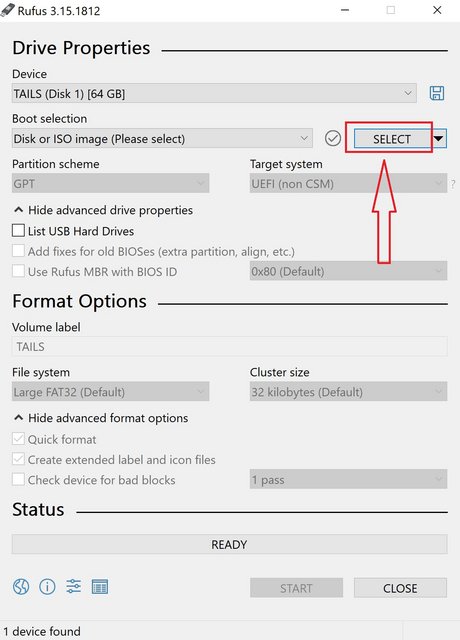
This will load the TAILS image into the “Boot Selection” menu:

Nothing else needs to be selected or changed, we can move to the bottom of RUFUS window and select “Start”

Once the the ISO image is finished burning onto the flash drive, you will get a “Ready” green bar across the bottom
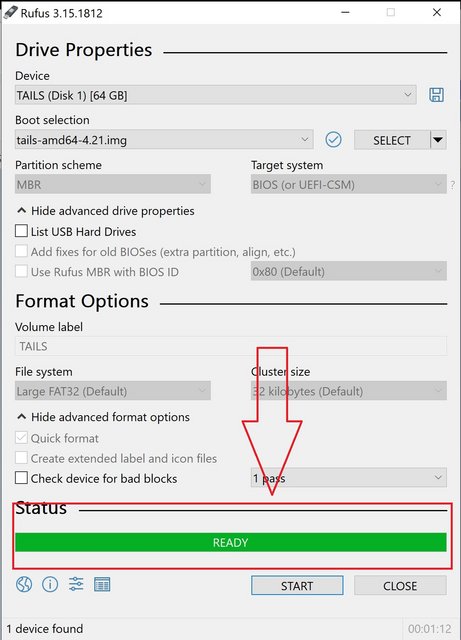
That’s it! You have yourself a TAILS flash drive ready to go.
By default, your TAILS flash drive will be non persistent, meaning that nothing will save onto the flash drive if you shut down using it. To make it persistent and save the settings and downloaded files, follow the instructions on the TAILS OS upon bootup into the flash drive.
Regards




[…] It is free and available in Windows, Mac, Linux, and Android. It is also native on the TAILS Operating System (meaning, it is part of the TAILS package when you set that […]
I’m trying to access the tutorials for the TOR browser and the TAILS OS and your security pictures keep asking for more and more selections…is it broken? Or how many do we have to go through to get to the tutorial?
It’s not doing that to me, so I’ll dig around on the admin side of the website to see if there are settings where I might be able to ‘relax’ some of the Captcha items. Haven’t had this reported before. -JJS
Sadly it won’t run on a pi…..yet 🙁
[…] https://radiofreeredoubt.com/2021/08/29/setting-up-tails-portable-secure-operating-system/ […]